Cybersecurity: Protect Your Digital Life
When working with Cybersecurity, the practice of defending computers, networks, and data from attacks, theft, or damage. Also known as information security, it’s the backbone of safe online activity. Today, almost every interaction—banking, chatting, shopping—relies on a solid security foundation. Without it, personal info, corporate secrets, and even national infrastructure are exposed to hackers. That’s why understanding the core concepts and the tools that strengthen them is essential for anyone who uses the internet, whether you’re a casual user or a tech professional.
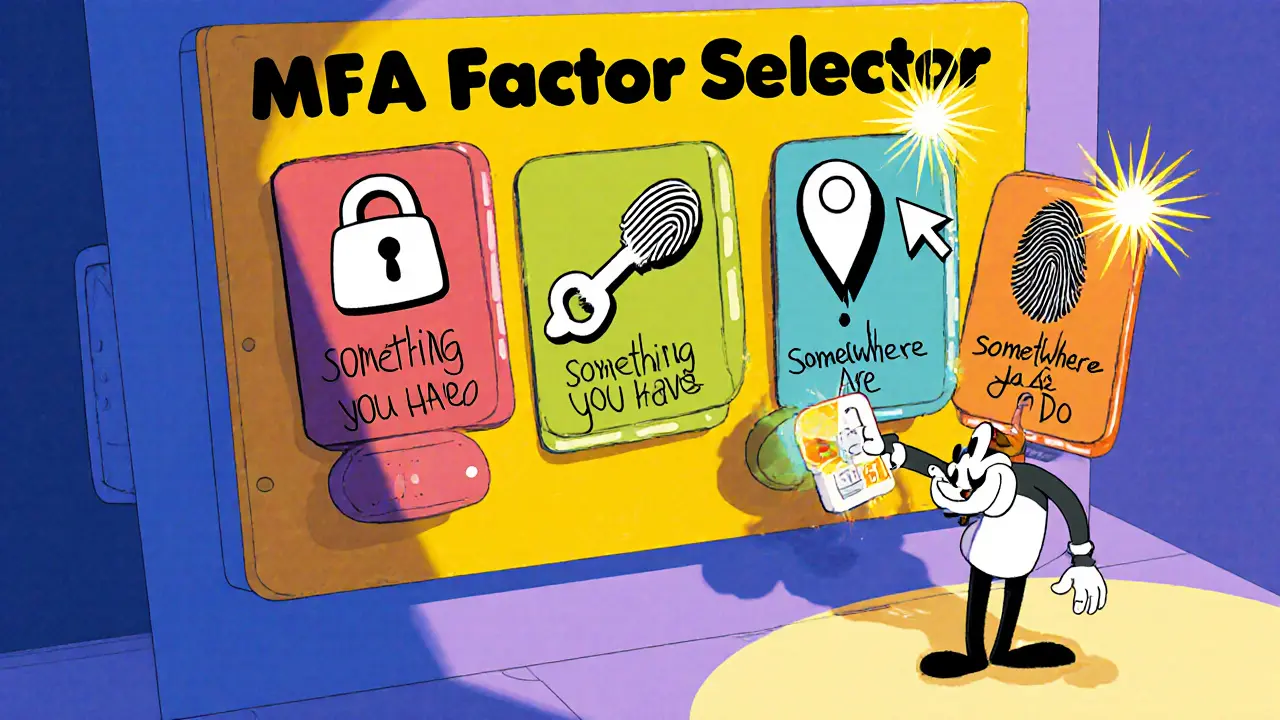
One of the most effective ways to harden your defenses is through Multi-Factor Authentication, a security method that requires two or more verification factors beyond a simple password. By adding something you know (a PIN), something you have (a smartphone app), or something you are (a fingerprint), MFA makes it dramatically harder for attackers to gain access. Passwordless Security, an approach that eliminates passwords entirely in favor of credentials like biometrics or hardware keys takes the idea a step further, removing the weakest link in the chain. Both strategies Cybersecurity relies on, and they boost protection by requiring multiple, independent verification steps. When you combine MFA with passwordless methods, you create a layered barrier that stops most credential‑stuffing and phishing attacks in their tracks.
Beyond MFA and passwordless options, emerging techniques such as Biometrics, verification methods that use unique physical traits like fingerprints, facial patterns, or voice and Behavioral Analytics, systems that monitor user behavior to spot anomalies and potential threats are reshaping how we think about digital safety. Biometrics adds a personal, hard‑to‑replicate factor, while behavioral analytics watches for irregular login times, device changes, or unusual transaction patterns. Together, they give security teams real‑time signals to block suspicious activity before it escalates. As cyber threats evolve, integrating these tools into your security stack ensures you stay ahead of the curve. Below you’ll find a curated collection of guides and deep dives that walk you through setting up MFA, adopting passwordless solutions, and leveraging biometrics and analytics to lock down your assets.