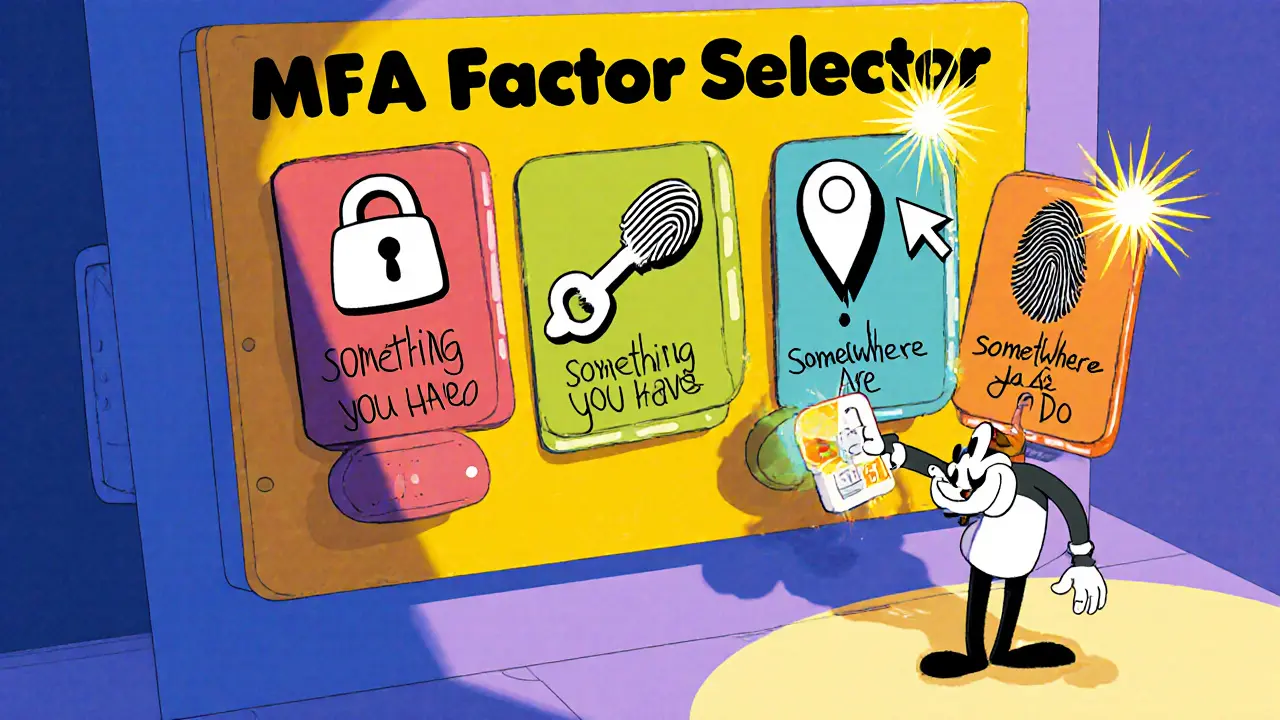
MFA Factor Selector
Select up to 3 authentication factors to build a secure MFA configuration. Each factor category provides different security benefits.
Something You Know
Passwords, PINs, security questions
Something You Have
Hardware tokens, OTP apps, SMS codes
Something You Are
Fingerprint, facial recognition, voice
Somewhere You Are
GPS location, IP address, geofencing
Something You Do
Typing rhythm, mouse movement, behavior
Selected Factors
Security Comparison
| Aspect | 2FA | MFA (3+ factors) |
|---|---|---|
| Number of factors | Exactly two | Three or more |
| Security strength | Moderate - vulnerable to phishing or SIM-swap | High - attacker must compromise multiple independent vectors |
| Usability impact | Low to moderate friction | Varies - can be seamless with push or biometric |
| Compliance coverage | Meets basic requirements | Required for regulated data (HIPAA, PCI-DSS, NIST 800-63B) |
Recommendation
Your selected combination provides strong security by requiring multiple independent verification methods. This significantly reduces the risk of unauthorized access even if one factor is compromised.
When you hear Multi-Factor Authentication is a security approach that requires two or more distinct verification methods to confirm a user’s identity. it often feels like the next logical step after relying on passwords or a simple text code. While Two-Factor Authentication (2FA) gives you a second layer, multi-factor authentication opens the door to a whole menu of checks that can stop attackers even when one factor is compromised.
Why 2FA Isn’t Enough Anymore
Cyber‑attackers have become experts at bypassing the most common 2FA methods. Phishing emails that pull a one‑time password (OTP) straight from a user’s phone, SIM‑swap tricks that hijack SMS codes, and credential‑stuffing bots that automate password‑OTP combos all erode the safety promised by a simple two‑step login.
According to the Cybersecurity and Infrastructure Security Agency (CISA), relying on a single factor is “a bad practice” because it leaves doors wide open for these modern tactics. The agency now recommends that organizations adopt a layered approach that can survive the loss of any single factor.
What Counts as an Authentication Factor?
- Something you know - passwords, PINs, or security questions.
- Something you have - hardware tokens, OTP apps, SMS codes, or push notifications.
- Something you are - fingerprint scans, facial recognition, voice authentication.
- Somewhere you are - GPS‑derived location, IP address, or network‑based geofencing.
- Something you do - typing rhythm, mouse movement patterns, or other behavioral cues.
Each of these categories can be combined in countless ways, letting security teams design a flow that matches the sensitivity of the data they protect.
Building a Real‑World MFA Deployment
- Identify the assets that need protection - financial records, source code, HR data, etc.
- Map the risk profile for each asset. High‑value resources merit three or more factors.
- Select strong factors for each step. A common trio is password + OTP app + fingerprint.
- Integrate the MFA service with your identity provider (Azure AD, Okta, etc.).
- Run a pilot with a small user group, collect feedback on usability, and adjust the flow.
- Roll out organization‑wide, monitor authentication logs for anomalies, and fine‑tune policies.
Microsoft explains that adding a third factor such as a biometric scan makes it practically impossible for an attacker who only has the password and OTP to gain entry. That extra hurdle is what separates a good MFA deployment from a simple 2FA overlay.
2FA vs. MFA: A Side‑by‑Side Look
| Aspect | 2FA | MFA |
|---|---|---|
| Number of factors | Exactly two | Two or more (often three‑plus) |
| Typical factors | Password + OTP (SMS, email, app) | Password + OTP + Biometric + Location + Behavior |
| Security strength | Moderate - vulnerable to phishing or SIM‑swap | High - attacker must compromise multiple independent vectors |
| Usability impact | Low to moderate friction | Varies - can be seamless with push or biometric, higher friction if many steps |
| Compliance coverage | Meets basic requirements for many standards | Often required for regulated data (HIPAA, PCI‑DSS, NIST 800‑63B) |
The table makes it clear that the extra layers in MFA are not just a marketing buzzword - they translate into measurable risk reduction. In a breach simulation, an organization that relied on password + SMS OTP saw 65% of compromised credentials lead to full account takeover, while the same scenario with an added fingerprint scan dropped that figure to under 5%.

Choosing the Right Factors for Your Environment
Not every factor fits every use case. Here’s how to decide:
- Hardware tokens (e.g., YubiKey) provide near‑immune resistance to phishing but involve a physical device that can be lost.
- Mobile authenticator apps (Google Authenticator, Authy) are cost‑effective, yet users may complain about the extra tap.
- SMS OTP is familiar but vulnerable to SIM‑swap attacks; best used as a fallback.
- Push notifications strike a balance - users just approve a login on their phone, and the server can embed device metadata for risk analysis.
- Biometrics like fingerprint or facial recognition add something you are, but you need devices that support the sensor and a privacy policy for data handling.
- Behavioral analytics (typing cadence, mouse movement) run in the background and can flag anomalous logins without user friction.
Turn‑key Technologies warns that an MFA system is only as strong as its weakest factor. Pairing a weak password with a strong biometric still leaves the password as an attack surface, so it’s wise to enforce robust password policies or move toward password‑less solutions where possible.
Cost and User Experience: Finding the Sweet Spot
Enterprise‑grade MFA can be pricey if you buy hardware tokens for every employee. Cloud‑based MFA services (Okta, Duo, Azure MFA) often charge per active user per month and include push, biometrics, and risk‑based analytics in the subscription. Small teams might opt for free authenticator apps combined with a modest biometric rollout on laptops that already have fingerprint readers.
But don’t forget the hidden cost of user resistance. A convoluted login flow can lead to help‑desk tickets, work‑arounds, or even outright avoidance of security policies. Aim for a friction level where the extra step feels natural - push approval or fingerprint scan usually win over manual code entry.
The Future: AI‑Powered Authentication
Artificial intelligence is reshaping MFA by analyzing dozens of data points in real time. Instead of asking a user for a second factor every time, an AI engine can decide whether the login looks “normal.” If the system detects a new device, unusual location, and a rapid typing speed, it will prompt for a biometric or a hardware token. If everything matches the user’s historical pattern, it may let the session pass with just the password.
Microsoft’s latest Azure AD conditional access policies already incorporate risk‑based triggers, and many vendors promise a future where “something you do” becomes the dominant factor, reducing reliance on passwords and OTPs altogether.
Quick Checklist for Moving Beyond 2FA
- Audit existing authentication flows - note where only 2FA is used.
- Classify data sensitivity and map required factor count.
- Pick at least one factor from a different category (e.g., biometric + hardware token).
- Test the chosen combination with a pilot group.
- Roll out with clear user communication and support resources.
- Monitor logs for failed attempts and adjust risk policies.
- Plan for future AI‑driven risk analysis as an optional upgrade.
Frequently Asked Questions
Is 2FA considered MFA?
Yes. Two‑Factor Authentication is a subset of Multi‑Factor Authentication because it uses exactly two distinct factors. MFA simply broadens the definition to include three or more.
What’s the most secure factor to add after a password?
Hardware‑based tokens or built‑in biometric sensors provide the strongest resistance to phishing and replay attacks. They are also independent of the network, making them hard to intercept.
Can I implement MFA without buying new devices?
Yes. Many cloud MFA providers let you combine existing smartphones (authenticator apps, push notifications) with built‑in laptop fingerprints. This approach keeps costs low while still adding a third factor.
How does behavioral authentication work?
The system records patterns like typing speed, mouse movement, and typical login times. When a session deviates from the baseline, the platform challenges the user with an extra factor.
Are there compliance rules that force MFA?
Regulations such as PCI‑DSS, HIPAA, and NIST SP800‑63B require multi‑factor authentication for access to sensitive data. Using only a password or a single OTP would not meet those standards.

Alex Gatti
October 5, 2025 AT 08:25MFA is the future no doubt
Bhagwat Sen
October 7, 2025 AT 02:05I’ve watched 2FA crumble under a simple phishing lure, so we need more than just a code. Pairing a hardware token with a biometric creates independent barriers that attackers can’t easily bypass. Users still get a smooth flow when push notifications replace manual entry. Skipping the extra factor is basically an invitation for compromise.
Marc Addington
October 8, 2025 AT 19:45If you’re still using just password + SMS you’re practically handing over the keys to the enemy.
Ciaran Byrne
October 10, 2025 AT 13:25Good overview, especially the part about blending hardware tokens with biometrics.
Brooklyn O'Neill
October 12, 2025 AT 07:05I appreciate the clear checklist; it’ll help our team move beyond basic 2FA quickly.
Lurline Wiese
October 14, 2025 AT 00:45When I first rolled out MFA at my startup, the panic in the help‑desk was palpable – everyone feared a login apocalypse. Yet after we introduced fingerprint scans combined with a YubiKey, the ticket volume dropped like a stone. It felt like we’d unlocked a secret level of security without sacrificing user happiness. The only drama left was bragging about zero breaches for six months straight. Seriously, if you’re still on SMS codes, you’re living in the past.
Adarsh Menon
October 15, 2025 AT 18:25Oh great another “MFA” hype train – as if passwords were ever safe. Sure, add a fingerprint and hope the sensor isn’t broken.
Rob Watts
October 17, 2025 AT 12:05Push‑based MFA feels like a tap, no hassle.
Cathy Ruff
October 19, 2025 AT 05:45Your “good overview” is half‑baked; you completely ignored the surge in supply‑chain attacks targeting hardware tokens.
Amy Harrison
October 20, 2025 AT 23:25This guide makes MFA feel approachable 😊 especially the checklist – can’t wait to try it out!
Miranda Co
October 22, 2025 AT 17:05People love fancy tables but forget most breaches start with phishing.
Amal Al.
October 24, 2025 AT 10:45Indeed, adding a biometric layer not only raises the security bar but also enhances user confidence; the balance between friction and protection is crucial, and push notifications can serve as a seamless bridge.
Natalie Rawley
October 26, 2025 AT 03:25Let me tell you, the hype around “behavioral analytics” is overblown – it’s just another way to collect data and sell it. You’ll spend months tuning models only to see marginal gains. Meanwhile, a simple YubiKey does the job without the privacy nightmare. The industry loves to market “AI‑powered MFA” as the next big thing, but most of it is smoke and mirrors. Bottom line: stick to proven factors.
John Corey Turner
October 27, 2025 AT 21:05Security is not a static checklist; it is a living philosophy that mirrors the complexity of human identity. When we speak of MFA, we are not merely stacking random mechanisms, we are weaving a tapestry where each thread reinforces the others. A password provides something you know, but it is frail in the face of credential stuffing. Adding something you have-be it a hardware token or an authenticator app-introduces a physical barrier that attackers must acquire. Yet even tokens can be intercepted through sophisticated man‑in‑the‑middle attacks if the provisioning process is weak. The third factor, something you are, such as a fingerprint or facial scan, leverages unique physiological traits that are incredibly difficult to replicate. However, biometric data carries privacy concerns; once compromised, you cannot simply reset your fingerprint. The fourth factor, somewhere you are, adds contextual awareness by checking IP reputation or GPS coordinates, which can flag anomalous logins instantly. A fifth factor, something you do, captures behavioral patterns like typing cadence, offering continuous authentication that adapts over time. By combining these diverse categories, an organization creates a defense-in-depth strategy that forces an attacker to compromise multiple independent vectors, exponentially increasing the effort required. Moreover, modern identity platforms allow adaptive risk assessments, presenting additional challenges only when the environment deviates from the baseline. This approach not only satisfies regulatory mandates such as PCI‑DSS and HIPAA but also aligns with a proactive security mindset. In practice, the user experience can remain fluid; push notifications and biometric prompts often happen in a fraction of a second. The key is to prioritize factors that align with the threat model and the user’s device ecosystem. Ultimately, MFA is a journey rather than a destination, and each added layer should be measured against both security gain and usability cost.
Katherine Sparks
October 29, 2025 AT 14:45Thank you for the comprehensive overview; the distinction between hardware tokens and biometric factors is particularly clear 😊. Your emphasis on risk‑based conditional access aligns well with current best practices.
Eva Lee
October 31, 2025 AT 08:25The epistemic synergy of multi‑vector authentication augments the threat surface reduction matrix, yet the latency introduced by continuous behavioral analytics must be calibrated against SLA thresholds.
Twinkle Shop
November 2, 2025 AT 02:05From a holistic governance perspective, the integration of heterogeneous authentication modalities demands a robust orchestration layer that can reconcile policy conflicts across legacy and cloud-native environments. By leveraging federated identity standards such as SAML and OIDC, organizations can abstract the underlying factor diversity while maintaining a consistent user experience. Additionally, the incorporation of geo‑fencing and device posture assessments enriches the confidence score used in adaptive access decisions. It is imperative that security architects document the risk taxonomy associated with each factor to satisfy audit requirements and to facilitate continuous improvement cycles. In sum, the strategic deployment of MFA should be viewed as an evolving ecosystem rather than a static control.
Greer Pitts
November 3, 2025 AT 19:45gotta say, the whole MFA thing feels like extra steps but it's worth it.
Jenise Williams-Green
November 5, 2025 AT 13:25While you romanticize “extra steps,” the moral imperative is clear: neglecting robust authentication endangers not just data but the very fabric of trust in our digital society.
Carthach Ó Maonaigh
November 7, 2025 AT 07:05Honestly, most of this MFA fluff is just marketing buzz; if you ask me, a good old password plus common sense is enough.